The Best of Mitigant Blog Articles in 2025


Happy New Year 2026! Throughout 2025, our blogs attracted significant engagement from cloud security practitioners, industry experts, and key stakeholders across the cybersecurity landscape. These results reflect our ongoing commitment to providing meaningful insights, strategic guidance, and practical recommendations on essential cloud security challenges to help organizations build and sustain a robust, resilient security posture.
We're thrilled to showcase the standout content from our website that connected most deeply with our readers this past year. What follows are the top ten blog articles, ranked by performance and reader engagement.
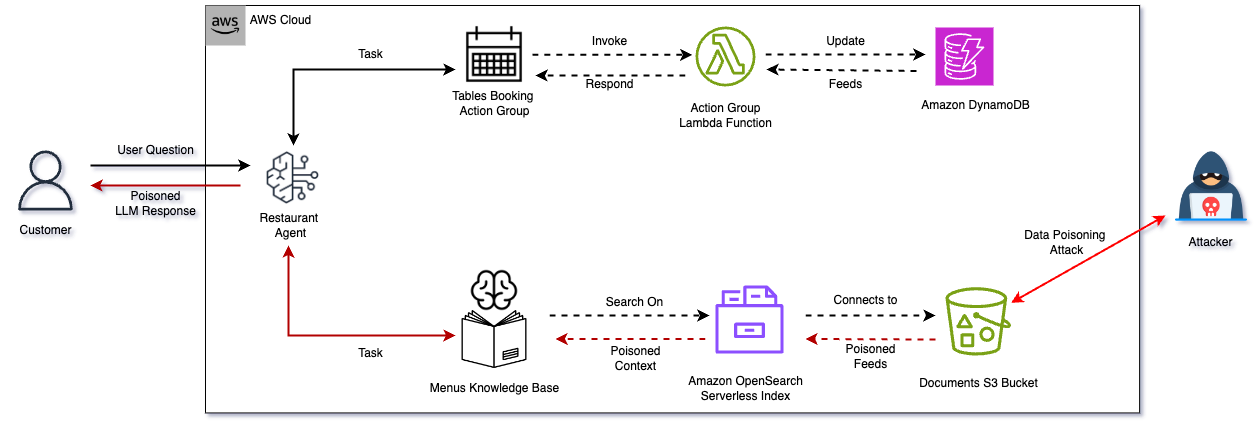
1. Bedrock or Bedsand: Attacking Amazon Bedrock's Achilles Heel
A remarkable achievement: This article has maintained the #1 position for two consecutive years (2024 and 2025), demonstrating its enduring relevance and impact on the cloud security community.
AI continued to dominate the technology landscape in 2025, with organizations increasingly leveraging Amazon Bedrock to power their AI applications. Amazon Bedrock provides access to several Foundation Models (FMs) from leading AI companies, making it an attractive choice for enterprises building AI-powered solutions.
However, as adoption accelerates, understanding the shared responsibility model and its specific application to Bedrock is imperative to maintaining a healthy cloud security posture. This blog post examined several critical security issues in Bedrock, including potential implications, detection opportunities, and mitigation strategies.
The article's sustained dominance reflects several important trends in the cybersecurity landscape:
Industry Recognition and Validation: Our research received significant recognition when Splunk incorporated our findings into its official AWS Bedrock Security Analytics Story, which directly references our work in its detection framework. This integration into enterprise security platforms validates the practical applicability of our research and demonstrates how our insights are being operationalized by security teams worldwide.
From Research to Defense: The article's real-world attack scenarios, including data poisoning attacks, prompt injection techniques, and LLMjacking, are grounded in our hands-on experience with Bedrock security testing. These aren't theoretical; they're based on actual attack emulation exercises and red teaming engagements we've conducted. Mitigant's platform includes corresponding attack scenarios that enable organizations to proactively test their Bedrock deployments through controlled emulation exercises, validating their defenses before adversaries exploit them.
Read the full article: Bedrock or Bedsand: Attacking Amazon Bedrock's Achilles Heel
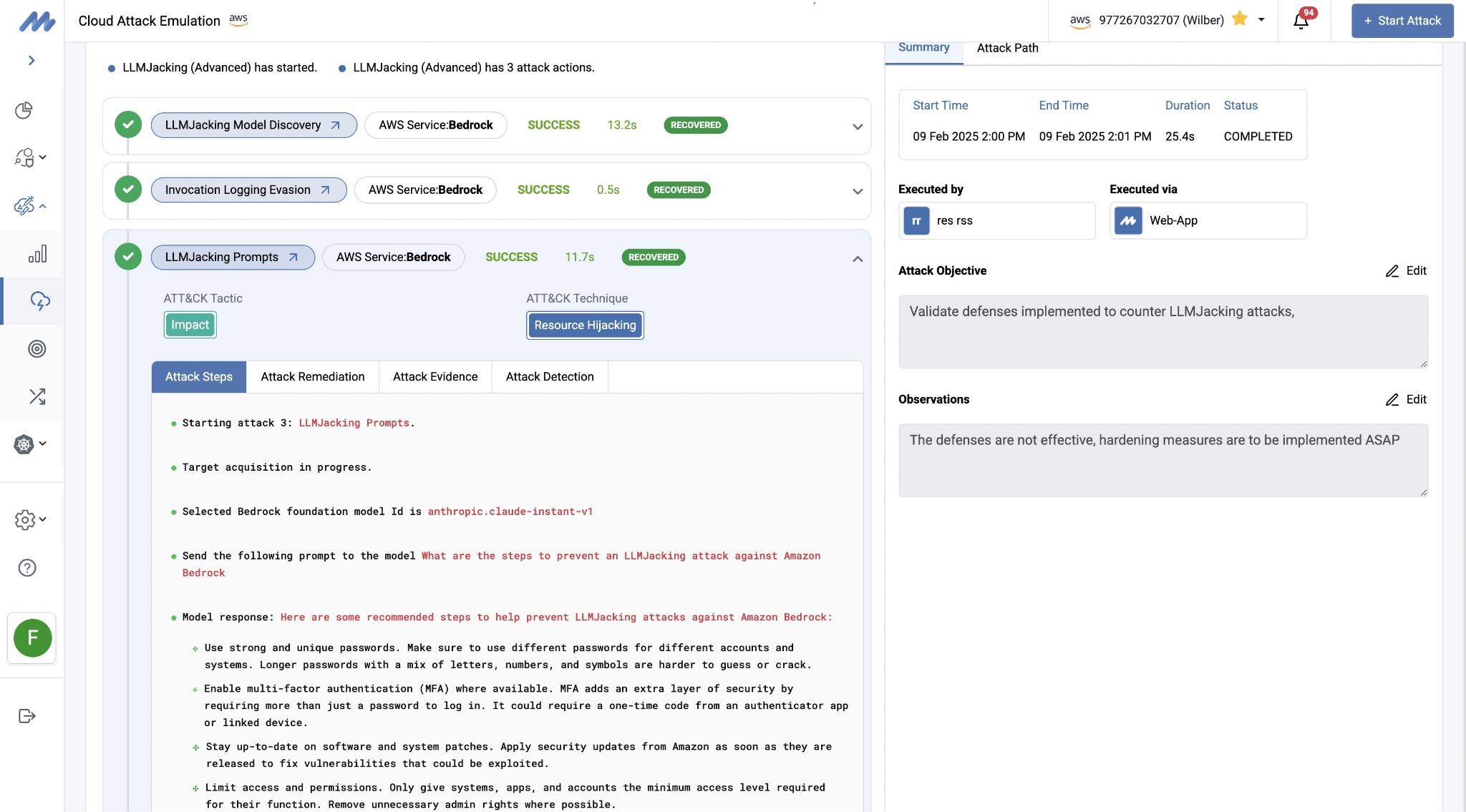
2. Demystifying Amazon Bedrock LLMJacking Attacks
Building on the momentum of our top-performing article, this piece provides an in-depth analysis of LLMJacking attacks targeting Amazon Bedrock deployments. As organizations deploy large language models at scale, adversaries have developed sophisticated techniques to hijack these resources for unauthorized use, leading to substantial financial and operational impacts.
Like its predecessor, this article draws directly from our operational experience conducting attack emulation and red teaming exercises against Bedrock environments. We break down the anatomy of LLMJacking attacks, demonstrating how attackers can abuse compromised credentials to exploit Foundation Models for their own purposes.
Mitigant's platform includes these LLMjacking attack scenarios, allowing security teams to safely emulate these threats in their own environments. Organizations can proactively test their detection capabilities, validate their incident response procedures, and verify that their security controls effectively prevent unauthorized use of models, all without risking actual compromise.
We explore detection strategies, forensic indicators, and defensive measures that security teams can implement to protect their GenAI infrastructure. The practical focus and actionable guidance, backed by real-world testing experience, made this article essential reading for organizations securing their AI workloads on AWS.
Read the full article: Demystifying Amazon Bedrock LLMJacking Attacks

3. Security Chaos Engineering 101: Fundamentals
This article is the first in a three-part series that provides the philosophical and technical foundation for the Mitigant platform.
Security Chaos Engineering (SCE) continued to gain traction in 2025 as organizations recognized the need to proactively test their security controls under realistic conditions. This foundational article positions SCE as integral to security engineering, not an esoteric craft, making it accessible to security engineers and cybersecurity professionals.
The principles and methodologies outlined in this series are not merely theoretical concepts; they represent the core architectural decisions and design philosophy that underpin every aspect of the Mitigant platform. When we built Mitigant, we didn't just implement SCE as a feature; we architected the entire platform around SCE principles: controlled chaos, empirical validation, assume-breach mindset, and safe experimentation with automated rollback.
The article addresses two critical misconceptions about SCE and offers a clear framework for understanding how controlled-chaos experiments can strengthen an organization's security posture. By demystifying the practice and presenting objective information, we help teams adopt SCE principles to validate their security assumptions before adversaries exploit them.
The growing interest in this article reflects the industry's shift from theoretical security assessments to empirical validation through adversarial exposure testing, a shift that Mitigant is pioneering in the cloud security space.
The complete Security Chaos Engineering 101 series:
- Security Chaos Engineering 101: Fundamentals - Establishing SCE as a security engineering discipline and addressing common misconceptions
- Security Chaos Engineering 101: Getting Your Hands Dirty - Practical implementation examples with real SCE experiments, including the mindset and intent required for successful chaos experiments
- Security Chaos Engineering 101: The Mind Map & Feedback Loop - The SCE mind map (what, why, who, how, where) and the feedback loop that enables continuous improvement through systems thinking
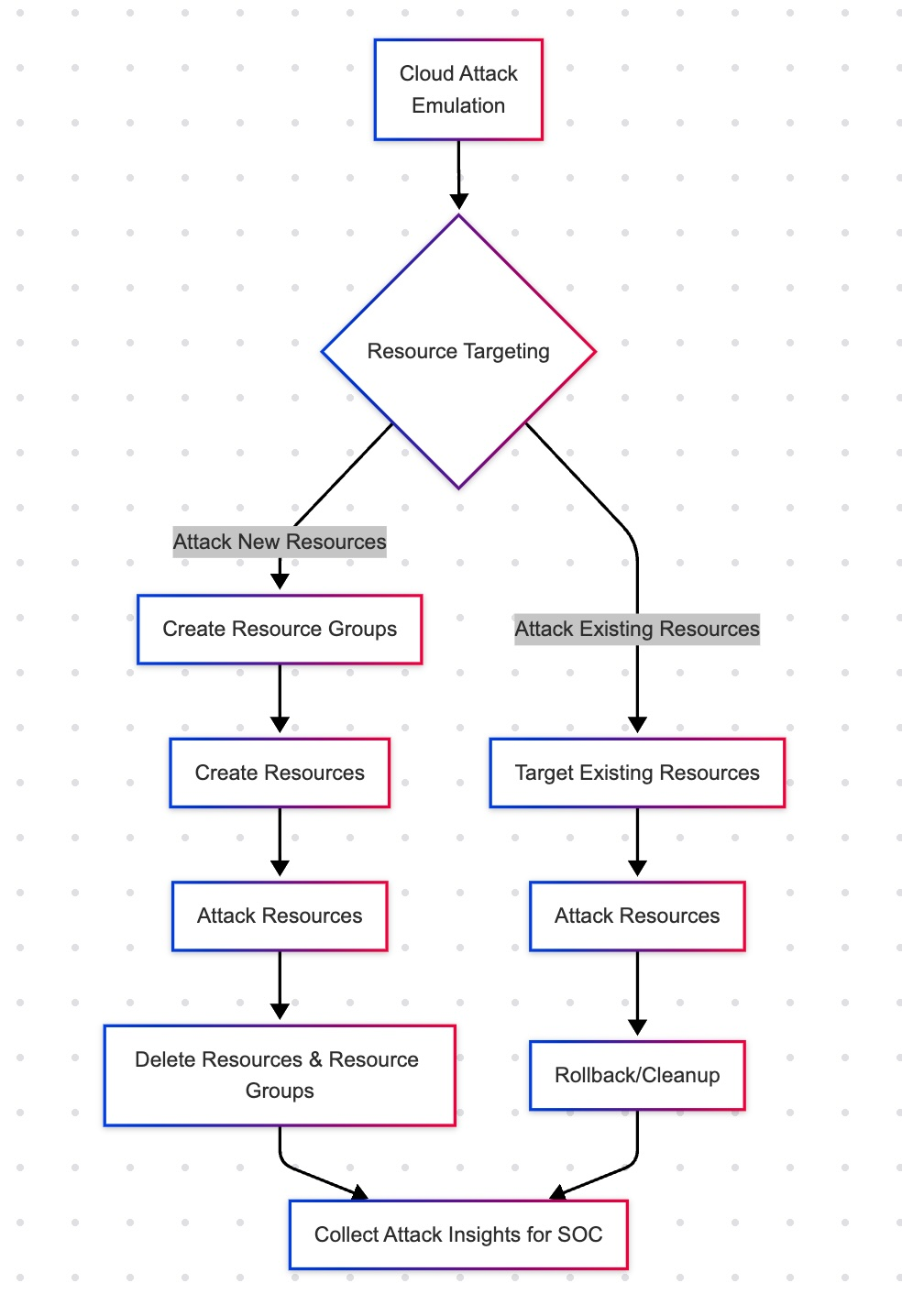
4. Feature Release: Cloud Attack Emulation for Azure
In 2025, we expanded Mitigant's Cloud Attack Emulation capabilities to Microsoft Azure in response to strong demand from our multi-cloud customers. This feature release article introduces comprehensive attack emulation scenarios designed specifically for Azure environments, enabling security teams to validate their Azure security controls through realistic adversarial testing.
The article details how organizations can safely execute attack scenarios against several Azure services, including EntraID, storage accounts, and virtual machines, without disrupting production workloads. This capability allows teams to identify exploitable misconfigurations and validate their detection capabilities across their Azure estate.
The enthusiastic response to this release demonstrates the critical need for platform-specific attack emulation tools as organizations increasingly adopt multi-cloud architectures.
Read the full article: Feature Release: Cloud Attack Emulation for Azure
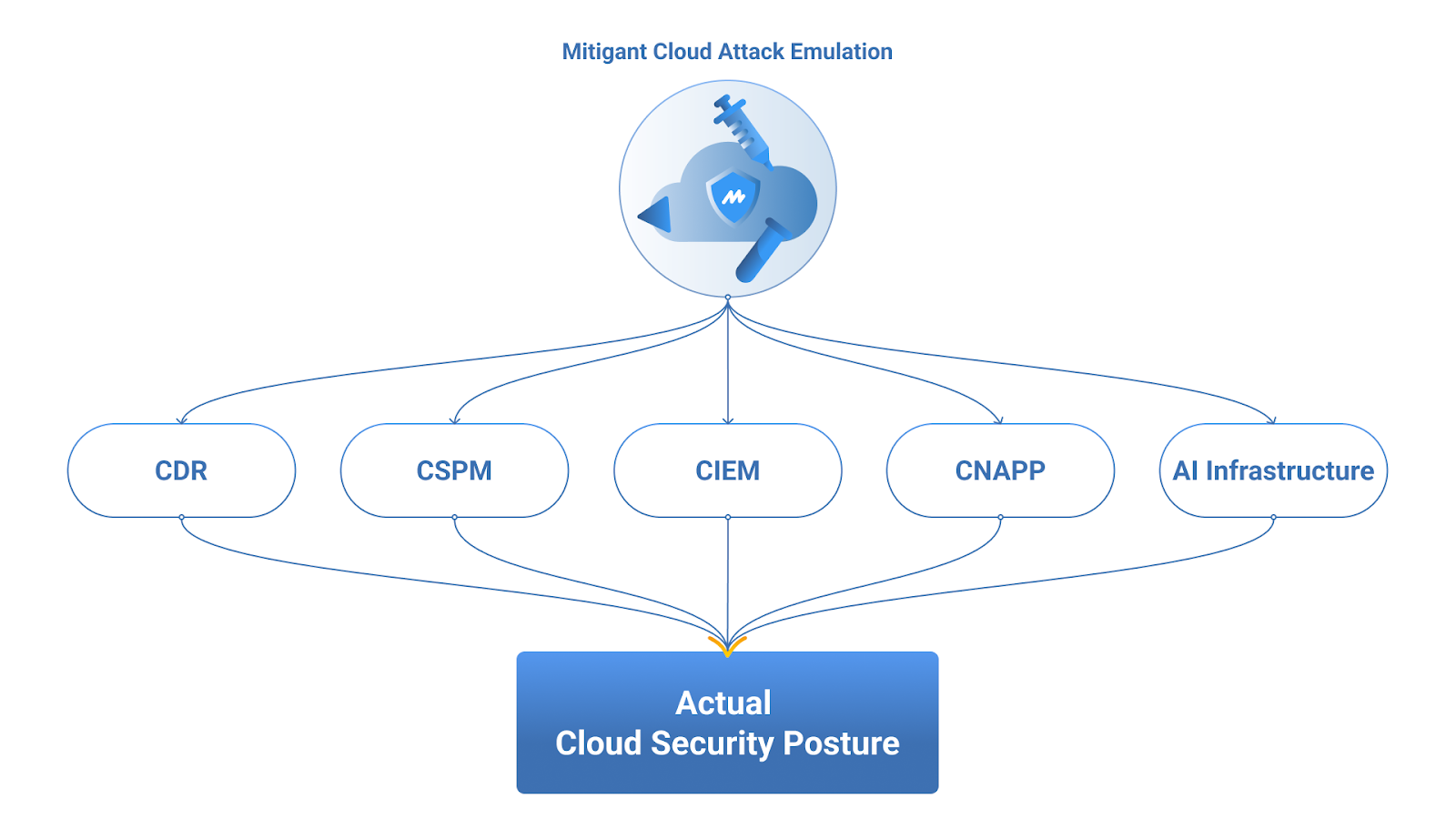
5. Cloud Attack Emulation 101: Getting Started
This article is Part 1 of the Cloud Attack Emulation 101 series, an educational journey into the practical application of adversarial emulation for cloud security.
As organizations began their journey with Cloud Attack Emulation, this getting-started guide provided essential foundation knowledge for security teams new to the discipline. The article walks readers through the fundamental concepts, methodologies, and best practices for safely emulating cloud attacks in production environments.
From setting up initial attack scenarios to interpreting results and improving security posture based on findings, this comprehensive guide helped security teams take their first steps toward empirical security validation. The practical, step-by-step approach made complex concepts accessible to teams at various maturity levels, covering critical topics such as the devil's advocate mindset, use cases for incident response exercises, and strategies for getting started safely.
The sustained interest in this foundational content underscores the growing adoption of Cloud Attack Emulation as a core security practice and demonstrates the industry's hunger for actionable guidance on implementing adversarial testing.
The Cloud Attack Emulation 101 series:
- Cloud Attack Emulation 101: Getting Started (June 2025) - Foundational concepts, the devil's advocate approach, and how to get started safely with non-production testing and enumeration attacks
- Cloud Attack Emulation 101: Shallow Waters (October 2025) - Deep dive into attack building blocks, attack actions vs. scenarios, and how to evolve from theoretical coverage to empirical validation
- Cloud Attack Emulation 101: Part 3 (Coming Soon) - Stay tuned as we continue this series with advanced techniques and real-world implementation strategies
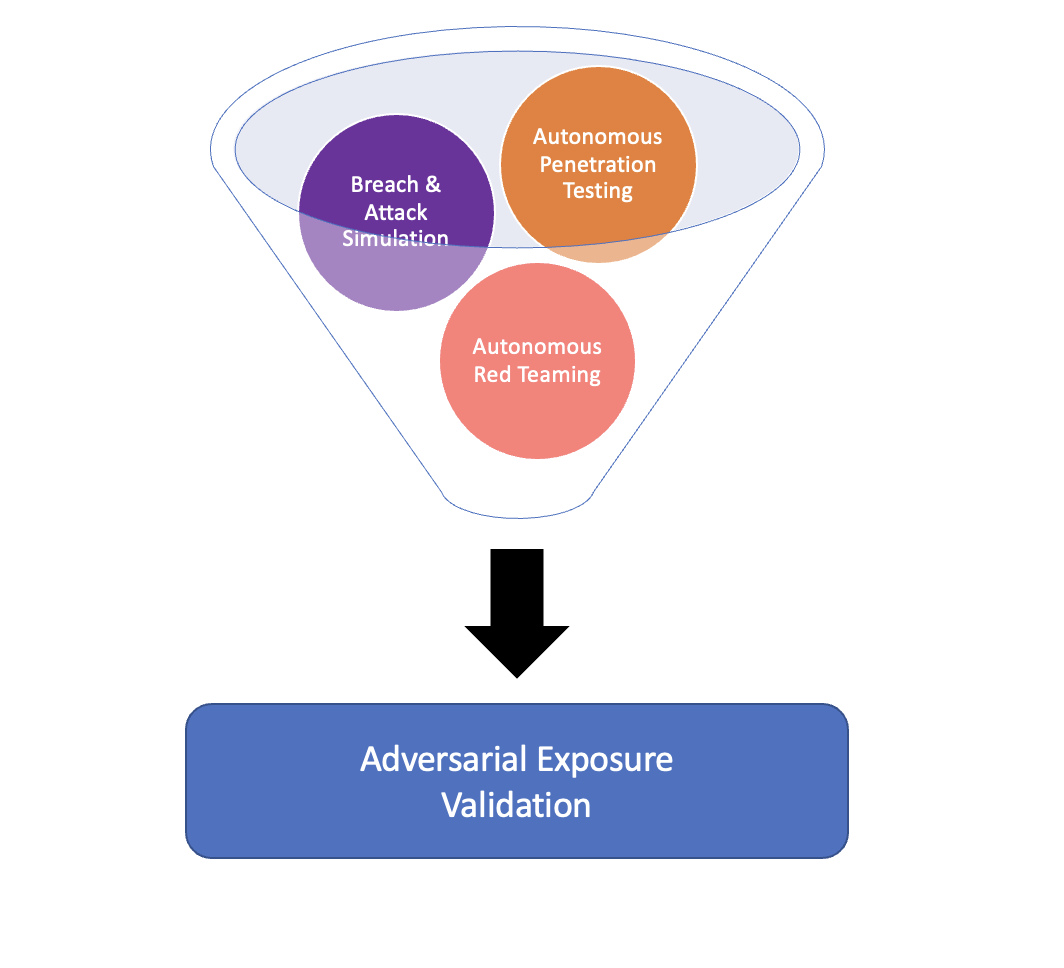
6. Rethinking Cloud Security Strategies with Adversarial Exposure Validation
Traditional cloud security approaches often rely on static configuration checks and theoretical risk assessments. This thought leadership article explores Adversarial Exposure Validation (AEV), a paradigm-shifting category introduced by Gartner that's transforming how organizations approach cloud security strategy.
As pioneers in the AEV space, we examine how this Gartner-defined approach moves organizations from "hope-based" security models to evidence-based approaches, where security controls are continuously validated through safe attack emulation. The article draws on our operational experience implementing AEV principles on Mitigant's platform, demonstrating the limitations of traditional CSPM tools and how empirical validation yields deeper insights into actual exploitability rather than theoretical vulnerabilities.
Gartner's recognition of AEV as a distinct security category validates what we've long advocated: that organizations need to move beyond scanning for misconfigurations to actually testing whether those issues are exploitable. This piece resonated strongly with security leaders and decision-makers seeking to transform their cloud security programs from reactive to proactive postures.
Read the full article: Rethinking Cloud Security Strategies with Adversarial Exposure Validation
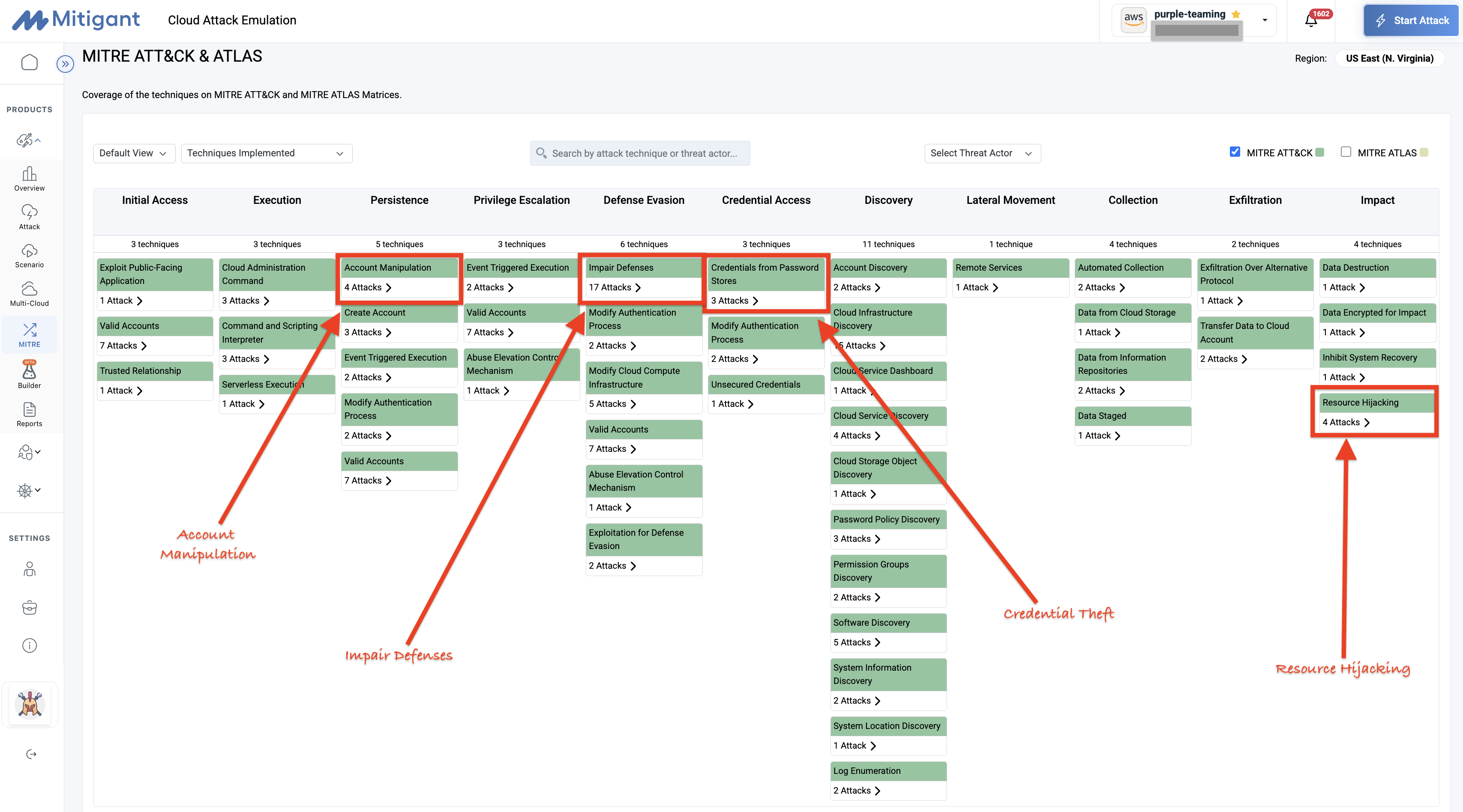
7. Demystifying The Most Pervasive Cloud Attack Techniques
This article analyzes findings from Red Canary's 2025 Threat Detection Report, translating industry threat intelligence into actionable cloud security guidance.
Cloud environments face a constantly evolving threat landscape, with certain attack techniques proving particularly effective across different cloud platforms. Red Canary's 2025 Threat Detection Report provided crucial insights into the techniques adversaries are actively deploying in the wild, and this article builds on that foundation with our operational perspective from conducting thousands of attack simulations.
We provide an in-depth analysis of the most pervasive cloud attack techniques observed in real-world incidents, helping security teams understand and defend against the tactics that adversaries actually use, not theoretical risks, but documented attack patterns from Red Canary's frontline detection data. From credential harvesting and privilege escalation to data exfiltration and persistence mechanisms, we examine each technique through the lens of the MITRE ATT&CK framework.
The article bridges threat intelligence with practical implementation by providing detection strategies and defensive recommendations that security teams can deploy immediately. More importantly, we show how Mitigant's Cloud Attack Emulation platform enables organizations to proactively test their defenses against these exact techniques identified by Red Canary, validating whether detection tools would actually catch these prevalent attacks.
The practical focus on real-world adversary behavior grounded in Red Canary's empirical data made this a valuable resource for threat-informed defense strategies.
Read the full article: Demystifying The Most Pervasive Cloud Attack Techniques
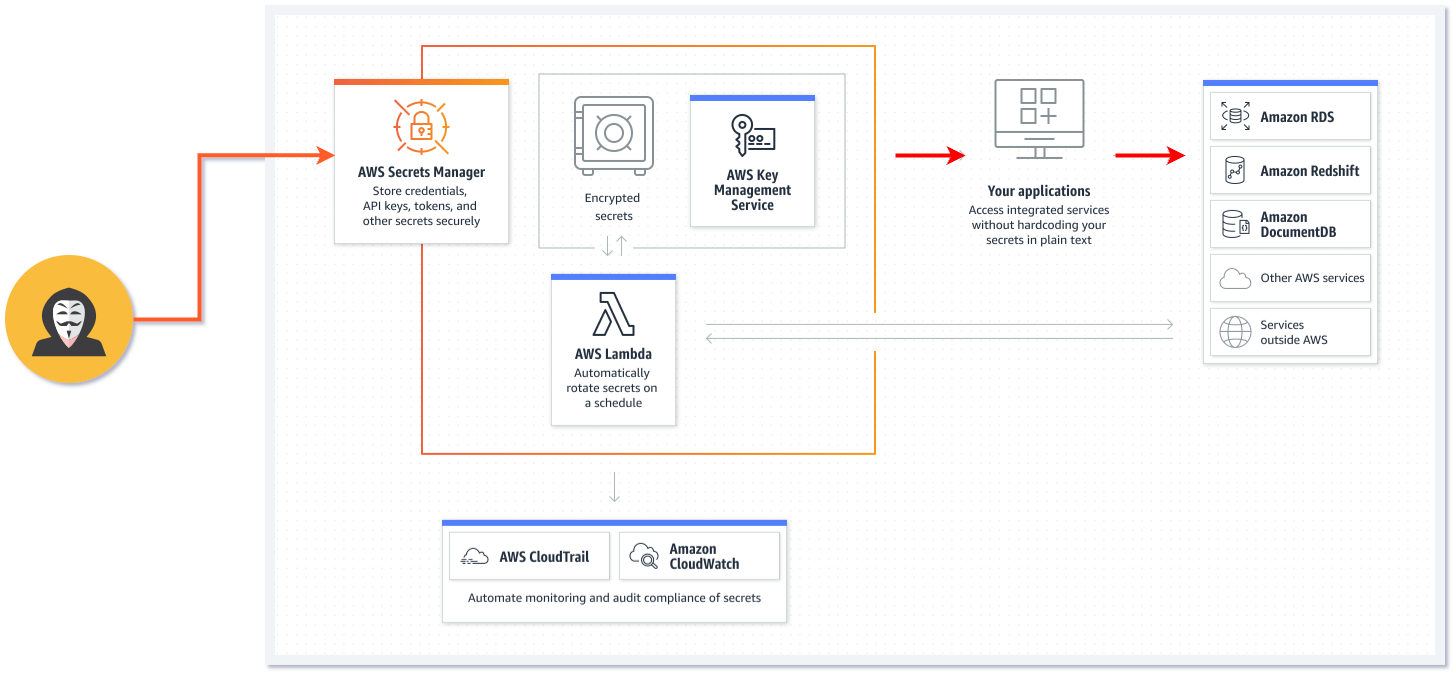
8. MITRE ATT&CK Cloud Matrix: New Techniques & Why You Should Care. Part I
The MITRE ATT&CK Framework has become an essential component of modern cybersecurity architecture, providing critical intelligence on attacker tactics and techniques that underpin effective defense strategies. When MITRE released the ATT&CK Framework v14 in October 2023, with over 18 new techniques, the cloud security landscape gained important insights into evolving adversary behavior.
This article examines two of the four new techniques relevant to the IaaS section of the MITRE ATT&CK Matrix for Enterprises, focusing on techniques that organizations encounter in real-world cloud compromises. We analyze Abuse Elevation Control Mechanism - Temporary Elevated Cloud Access and Credentials from Password Stores: Cloud Secrets Management Stores, demonstrating how sophisticated attackers leverage these methods to compromise cloud environments.
Rather than merely documenting these techniques in theory, the article bridges the gap between framework theory and practical security operations. We show how security teams can operationalize MITRE ATT&CK intelligence to guide their detection engineering, threat hunting, and incident response strategies. More importantly, we demonstrate how Mitigant's platform enables teams to proactively emulate these exact techniques in their environments, validating whether their security controls would actually detect these attacks before adversaries exploit them.
The sustained interest in this content reflects the ongoing relevance of threat intelligence frameworks as foundational tools for security practitioners building mature, threat-informed defense programs.
Read the full article: MITRE ATT&CK Cloud Matrix: New Techniques & Why You Should Care. Part I
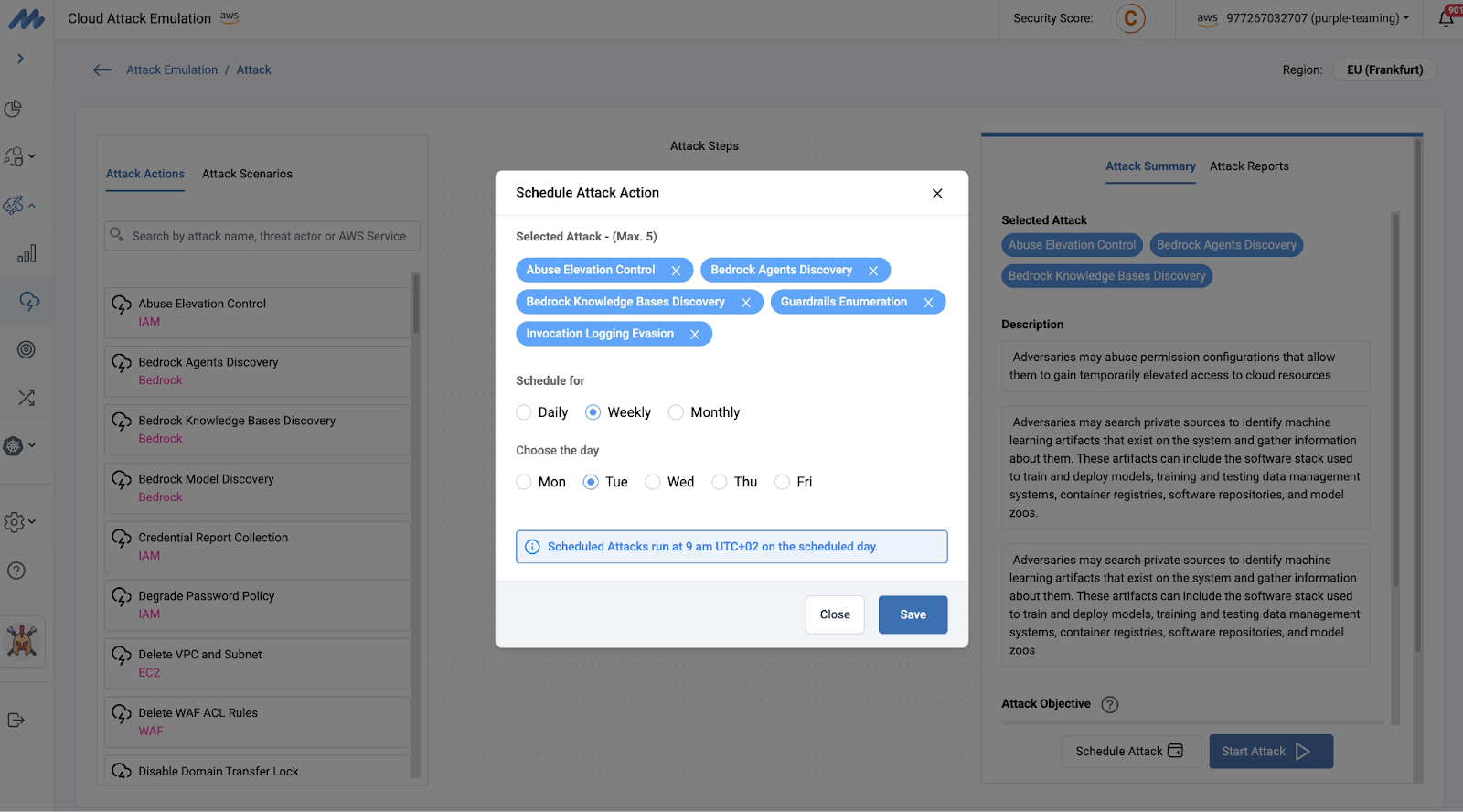
9. Feature Release: January 2025
Kicking off 2025 with transformative capabilities shaped by customer feedback, this release introduced four major features designed to help organizations implement Continuous Threat Exposure Management (CTEM) and integrate attack emulation into modern security workflows.
Attack-as-Code (AaC): This groundbreaking feature brings software engineering principles to offensive security, enabling repeatability, consistency, and manageability of security testing and validation. Built on the Mitigant API and leveraging GitHub Actions, AaC allows teams to seamlessly integrate adversary emulation into Detection-as-Code (DaC) pipelines.
Attack Scheduler: Automates the execution of security validation tasks, enabling security teams to run attacks on a daily, weekly, or monthly schedule. This automation frees up valuable time for security professionals while ensuring continuous validation of cloud resources, including IAM policies, encryption configurations, and logging mechanisms.
Kubernetes Vulnerability Prioritization: Recognizing that not all vulnerabilities pose equal risk, this feature helps teams focus remediation efforts on what actually matters. The platform now incorporates two industry-leading prioritization approaches: EPSS (Exploit Prediction Scoring System), which predicts the likelihood of a vulnerability being exploited in the wild based on real-world threat intelligence, and KEV (Known Exploited Vulnerabilities) from CISA's catalog of actively exploited vulnerabilities..
DefectDojo Integration: This integration bridges vulnerability management and attack emulation, enabling automated workflows in which identified vulnerabilities can be validated through real-world exploit attempts, providing empirical evidence of exploitability rather than theoretical assessments.
These features position Mitigant as a leader in implementing Gartner's CTEM framework, providing organizations with tools to continuously discover, prioritize, validate, and mobilize their security programs.
Read the full article: Feature Release: January 2025
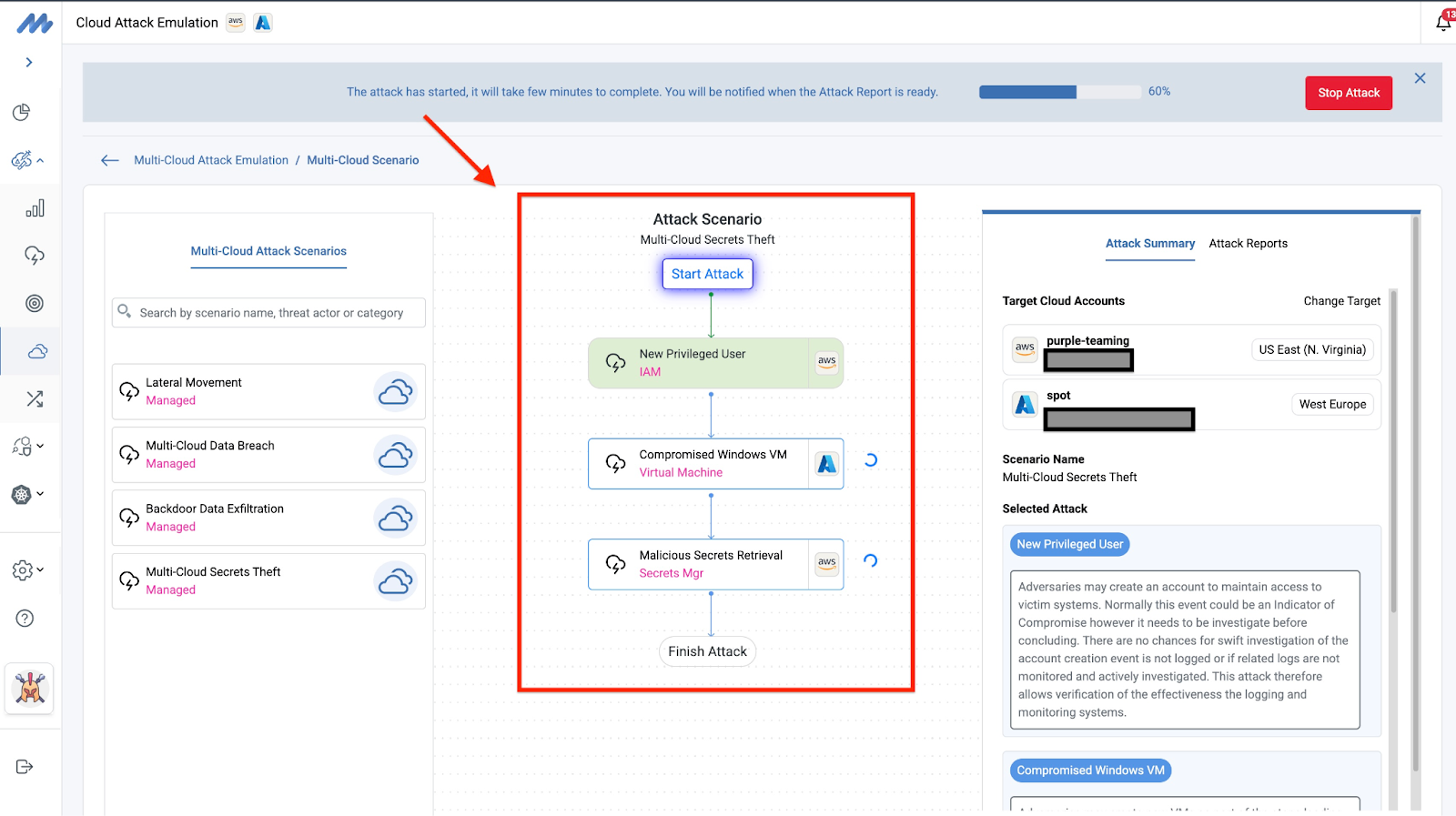
10. Feature Release: Multi-Cloud Attack Emulation
Rounding out our top 10, this feature release addressed a critical need for organizations operating across multiple cloud platforms. Multi-Cloud Attack Emulation enables security teams to execute coordinated attack scenarios across AWS and Azure environments, providing a unified view of security posture across their entire cloud estate.
The article explores how cross-cloud attack chains work in practice and demonstrates how Mitigant's platform helps organizations identify security gaps that only become apparent when testing across cloud boundaries. This capability is essential for enterprises with complex, heterogeneous cloud deployments.
The strong interest reflects the reality that most enterprises now operate in multi-cloud environments and need security solutions that can keep pace with this complexity.
Read the full article: Feature Release: Multi-Cloud Attack Emulation
Looking Ahead to 2026
As we reflect on 2025's top-performing content, several themes emerge: the growing convergence of AI and empirical security validation is fundamentally transforming cloud security. This year marked significant milestones in making sophisticated offensive security capabilities accessible, intelligent, and continuously operational.
AI-Powered Intelligence: We integrated AI across the platform, from intelligent attack report summarization to contextual attack recommendations. These AI capabilities don't just automate tasks they amplify security team expertise, enabling practitioners at all skill levels to conduct sophisticated security validation with unprecedented efficiency.
Attack Builder: Our innovative Attack Builder democratizes attack creation, allowing security teams to compose custom cloud attack scenarios without writing code. Currently in beta, this feature reflects our vision of making cloud attack emulation as intuitive as building a workflow, empowering security teams to test their unique threat models with point-and-click simplicity.
Attack-as-Code: By bringing software engineering principles to offensive security, we've enabled detection engineers and SecOps teams to integrate adversary emulation directly into their CI/CD pipelines. Attack-as-Code transforms security validation from periodic exercises into continuous, automated processes that keep pace with modern development velocity.
Automated Cloud Penetration Testing: The combination of scheduling, automation, and intelligent attack selection has transformed cloud penetration testing from expensive, infrequent engagements into continuous, cost-effective validation. Organizations can now maintain persistent offensive security postures without the traditional resource constraints.
These innovations reflect our unwavering commitment to the core principles that founded Mitigant: Security Chaos Engineering, empirical validation, and the belief that effective defense requires thinking like an attacker. As we move into 2026, we remain focused on pushing the boundaries of what's possible in cloud security validation making it more intelligent, more accessible, and more impactful.
Continue Your Journey
Explore More Insights: Dive deeper into cloud security research, threat analysis, and platform innovations on the Mitigant Blog. From technical deep-dives to strategic thought leadership, we publish actionable content that helps security teams stay ahead of evolving threats.
See Mitigant in Action: Discover how organizations across industries are transforming their cloud security postures with empirical validation. Visit our Customer Use Cases to see real-world implementations and results from companies leveraging Mitigant's platform.
Ready to Validate Your Defenses? Don't wait for a breach to discover your security gaps. Book a demo and see how Mitigant's Cloud Attack Emulation platform can help you move from hope-based security to evidence-based defense.






.png)
