Demystifying The Most Pervasive Cloud Attack Techniques


Organizations often improve their cloud security posture by implementing measures informed by industry trends. Reputable cybersecurity organizations often provide such trends based on real-world data and unbiased analysis. Red Canary recently released the Threat Detection Report 2025, derived from a deep analysis of over 93,000 threats detected across her customer environments, including devices and cloud infrastructure. This article explores the most prevalent cloud attacks discussed in the report and provides further insights and countermeasures.

Cloud Threat Detection - An Overview
The need to adopt efficient threat detection strategies in cloud infrastructure increases dramatically as the threat landscape evolves. Cloud security tools like CSPM, CIEM, and CNAPP provide organizations with compliance and basic cyber hygiene levels; however, implementing threat detection capabilities is imperative to thwart attacks becoming more commonplace, e.g., those outlined in the 2025 Red Canary Threat Detection report. Detecting these attack techniques could be tricky given that adversaries implement stealthy measures, e.g., using valid credentials. Hence, a solid understanding of these attack techniques is imperative for implementing appropriate countermeasures.
One way to quickly gain appreciable understanding of these cloud attack techniques is via cloud adversary emulation; this empowers security teams with practical understanding and also facilitates validation of the implemented countermeasures. Mitigant Cloud Attack Emulation (CAE) provides enterprise-grade cloud adversary emulation for organizations of all sizes to test several cloud attacks techniqes, including the ones mentioned in the Red Canary report. The following sections examine the most prevalent cloud attack techniques described in the report with additional insights and countermeasures.
Cloud Service Hijacking
Cloud Service Hijacking (T1496-004) is one of the report's top three techniques. The most prominent technique in this category is LLMJacking, an attack increasingly used by cyber criminals to compromise cloud-based LLMs, e.g., those provided by Amazon Bedrock. The increasing adoption of GenAI by organizations makes this attack very attractive for cyber criminals who use the hijacked models for illicit business to the detriment of the actual cloud account owners. According to Sysdig, compromised organizations could accrue bills up to $46,000/day. We extensively discussed the intricacies of LLMJacking in a previous blog post and also recorded a demonstration of the attack, available on Youtube.
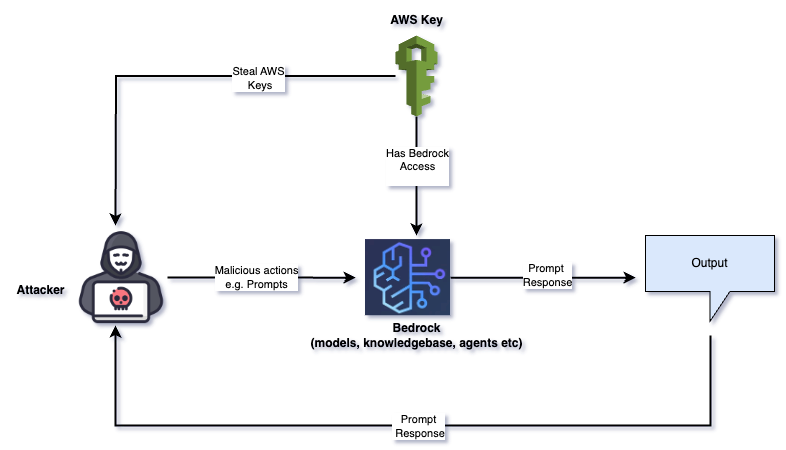
There are other Resource Hijacking (T1496) sub-techniques that also require some attention; for example, Compute Hijacking (T1496-001) is commonly used for cryptomining attacks against EC2 instances and Kubernetes environments. Attackers also use the Cloud service hijacking sub-technique for attacking messaging services like AWS SNS and SES, which are thereafter used for spamming, phishing, and SMS messaging. The Mitigant CAE provides several attacks that can emulate these techniques, e.g., Stop Cloudtrail, Invocation Logging Evasion, Stop Config Recorder, and Suspend GuardDuty.

Impair Defenses
Attackers often aim to remain under the radar once accessing a victim cloud environment. Efforts to achieve this stealthiness are called Impair Defenses techniques (T1562); these techniques constitute switching off security systems, e.g., Cloudtrail bucket logging. The cloud favors Impair Defenses techniques, given most security controls are an API call away. Fair enough, there are measures to reduce these risks, e.g., using this Amazon Web Services (AWS) Security Reference Architecture. One of the recommendations of the SRA is the restriction of critical security services in the “Security tooling account,” which would have very stringent access control guardrails. However, the security tooling account might not cover some resource-level configurations, e.g., S3 bucket logging and WAF ACL logging.

Consequently, security teams must implement additional measures that hamper Impair Defenses techniques, especially threat detection measures. Adversary emulation allows security teams to test and validate the efficiency of implemented security measures realistically. The Mitigant CAE has 13 attacks for emulating different Impair Defenses techniques across several AWS services, including EC2, EventBridge, Cloudtrail, S3, Bedrock, and Route 53.

Account Manipulation
Once in a victim cloud account, attackers aim to proceed to their objectives. Unfortunately for them, the credentials used for initial access often have limited privileges. Hence, privilege escalation becomes the next option, and a common technique to elevate privileges is Account Manipulation (T1098). There are several ways attackers implement Attack Manipulation, including modifying IAM policies, creating additional access keys for IAM users with higher privileges (Additional Cloud Credentials) and taking advantage of existing roles with higher privileges (Additional Cloud Roles).

Detecting the events generated due to these attack efforts could be tricky as valid credentials are often used. Ultimately, security teams need to be familiar with these events, contextual to their environments and validate whether threat detection tools and other cloud security tools are efficiently detecting/preventing these attack efforts. Mitigant CAE can be leveraged to emulate several Account Manipulation techniques to enhance holistic detection/response capabilities; including people, processes and technology aspects.

Credential Theft
Attackers require access to cloud accounts as a prerequisite for successful attacks, and this is commonly achieved through several Credential Access techniques (TA006), including collecting publicly (wrongly configured) credentials and stealing credentials from devices. However, an ecosystem is rapidly evolving, specializing in stealing and selling valid credentials to the highest bidder. The main characters behind this ecosystem are known as Initial Access Brokers (IAB), and they often work with Ransomware-as-Service (RaaS) providers, further lowering the bar for successful (ransomware) attacks.

Aside from IABs, attackers also look for credentials within cloud environments to achieve their objectives. Due to the need to automate several aspects of cloud applications and infrastructure, credentials are commonly retained in several stores, including secret managers. With valid credentials, attackers can access these credential stores and harvest credentials and other secret materials, see a more elaborate description in a past Mitigant blog article. Conequently, security teams must implement appropriate countermeasures and validate effectiveness using approaches like adversaery emulation. Mitigant CAE provides attacks that implement several credential access techniques, including Credentials from Password Stores (T1555), Modify Authentication Process, and Unsecured Credentials. These attacks span several AWS services, including Lambda, IAM, Secret Manager, EC2, and RDS thus empowering security teams to be agile and effective.

Empower CloudSecOps to Thwart Cloud Attacks
Enabling a resilient security posture requires a defense-in-depth strategy. However, organizations tend to focus on preventive security measures to the detriment of detective and recovery measures. With the proliferation of IABs and other evolving threats, preventive measures are drastically limited and provide a false sense of security at best.
Ultimately, security measures require continuous evaluation to detect blindspots promptly. Adversary emulation is a practical approach for realistically evaluating cloud security postures. Cloud security operation teams leverage adversary emulation to validate cloud security tools, such as CSPM, CDR, and CNAPPs. Adversary emulation is also beneficial for GenAI Red teaming, incident response/forensic investigation exercises, red/purple teaming exercises, and cloud penetration testing.
The Mitigant Cloud Attack Emulation has over 100 cloud attacks that organizations of differing sizes can safely leverage for these important security measures. These attacks, which include the techniques mentioned in the Red Canary report, are all mapped to MITRE ATT&CK and MITRE ATLAS frameworks and cover AWS and Azure. For more details, read our recent article.
Sign up for your free trial today. - https://www.mitigant.io/en/sign-up






.png)
